Security Audit
SolidProof conducts strict audits of smart contracts to identify vulnerabilities, enhance code quality, and optimize gas utilization. Our experienced team follows a rigorous methodology, delivering top-notch smart contract auditing services that prioritize security and reliability.
Techniques and methods
Structural Analysis
Structural Analysis
During the Structural Analysis phase, we examine the design patterns and structure of smart contracts to ensure that they are structured in a way that won't cause future issues. This involves thoroughly checking the smart contract's design patterns and structure.
Static Analysis
Static Analysis
We undertake a comprehensive static analysis to meticulously identify vulnerabilities within contracts. This crucial step involves leveraging a suite of cutting-edge automated tools calibrated to thoroughly test the security of smart contracts, leaving no stone unturned.
Code Review
Code Review
We conduct manual analysis of the code to identify new vulnerabilities and verify any vulnerabilities found during static analysis. We meticulously examine the contracts, thoroughly checking their logic against those described in the whitepaper.
Gas Consumption
Gas Consumption
During this phase, we evaluate the performance of smart contracts in a live environment. Our focus is on determining the amount of gas consumed and exploring ways to optimize the code for more efficient gas usage.
How to Audit
-
2
Begin of review
We start checking the code for vulnerabilities. We basically check all contracts manually line-by-line, of course we also use automatic tools for support.
-
3
Initial Audit report
As soon as all tests are completed, the team is informed about the vulnerabilities found and we assist in problem solving.
-
4
Complete Audit
After all vulnerabilities are fixed or acknowledged, a final audit report is issued.
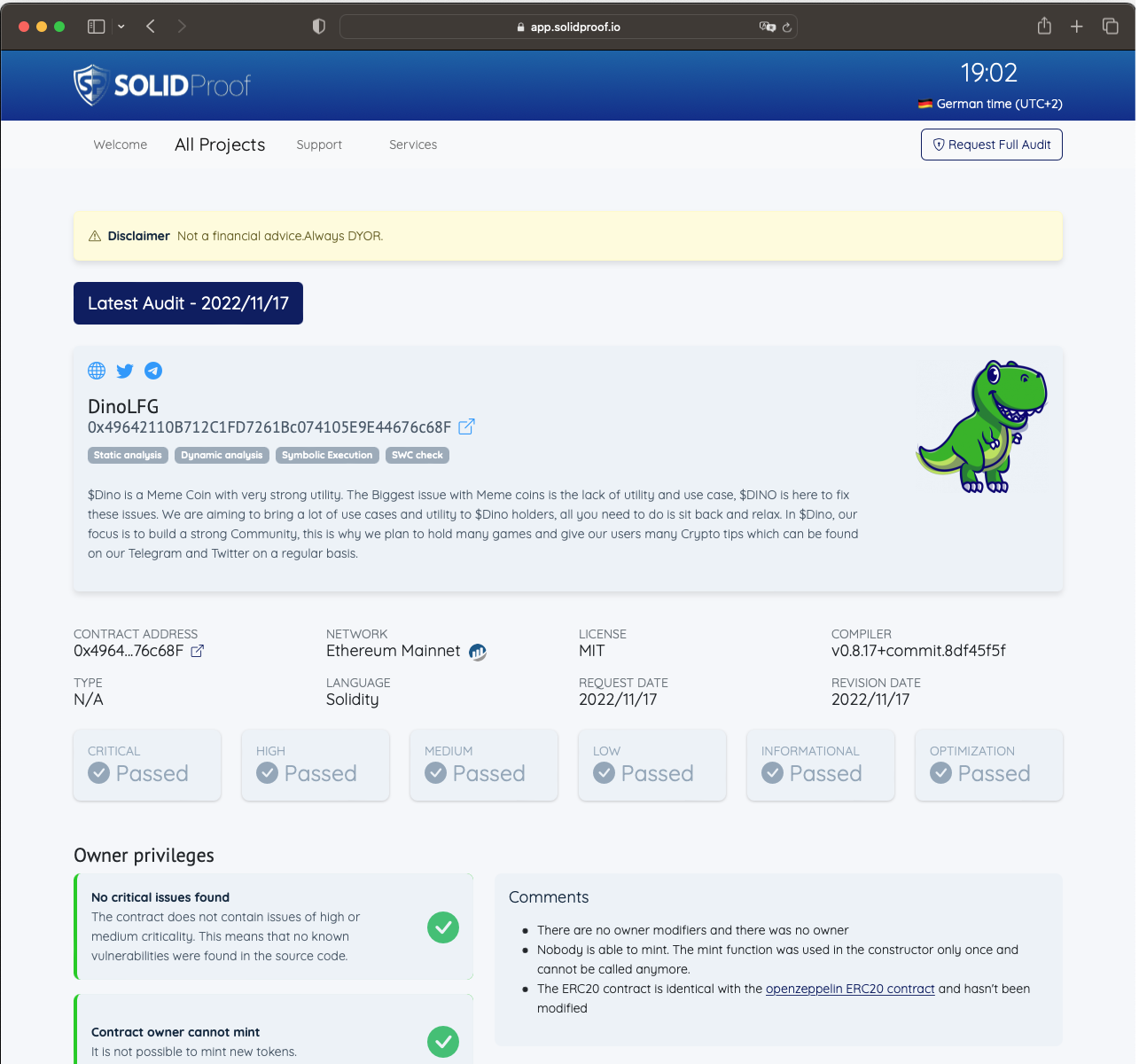
Vulnerability Checklist
Placeholder Adipisicing non labore exercitation fugiat irure amet aliquip aute est. Et eiusmod fugiat dolore qui id ipsum sunt eiusmod laborum officia veniam sint. Ex laborum nulla sint eiusmod sunt irure sit qui dolore velit. Do in sunt ex tempor nulla voluptate duis quis cillum tempor laboris officia. Culpa nisi exercitation aliqua eiusmod tempor exercitation anim officia eiusmod est fugiat. Veniam esse consectetur Lorem aliqua in in minim sit deserunt irure do Lorem incididunt ea. Ex adipisicing aliqua id voluptate est.
Need an audit?
Click on the button "Request an audit" to get in contact with the Solidproof team!